Difference between revisions of "Testing Firewalls and Web Proxies"
(→Configuring the firewall) |
(→Testing Protege) |
||
| Line 29: | Line 29: | ||
In this configuration, an unmodified copy of Protege on a virtual machine on the green network will not be able to connect to ontologies on the web and it will not be able to get updates from the network. But if you change the protege configuration as described in [[Working with firewalls and proxies]], Protege will again be able to both access ontologies on the web as well as get updates. | In this configuration, an unmodified copy of Protege on a virtual machine on the green network will not be able to connect to ontologies on the web and it will not be able to get updates from the network. But if you change the protege configuration as described in [[Working with firewalls and proxies]], Protege will again be able to both access ontologies on the web as well as get updates. | ||
| + | |||
| + | == Dealing with a pesky apple == | ||
Revision as of 13:36, July 12, 2013
Contents
Testing firewalls and proxies by using a virtual network
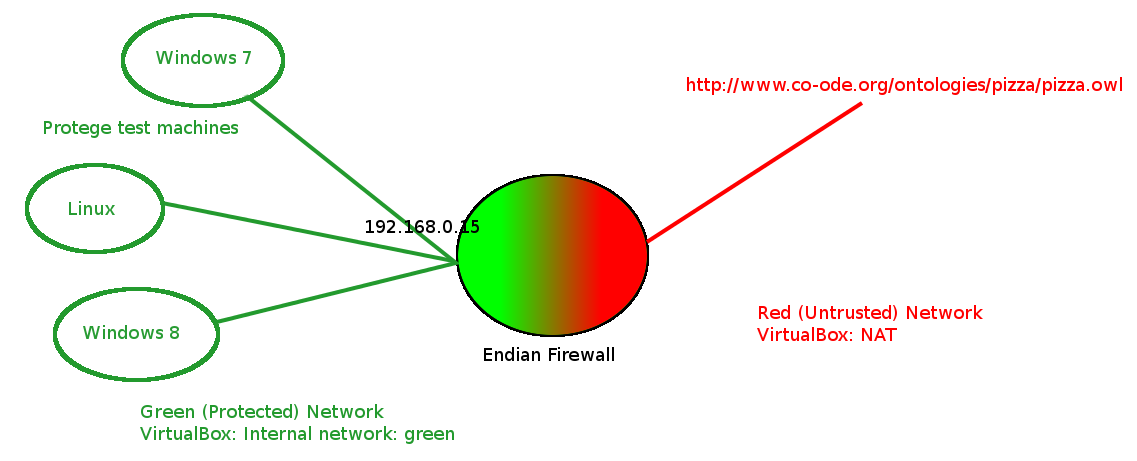
Occasionally we get questions from people who are behind a firewall. In the past, we have had no way to simulate and test how Protege behaves in their environment and so our answers on the mailing list have been somewhat limited. But with a virtualization software such as vmware or VirtualBox, it is not too difficult to simulate such a network configuration and test how Protege behaves. In this particular case, I think that it is even possible to work with Mac OS X, which is a generally difficult platform for developers to work with. In this case the problem is that os x does not run very well in virtual machine. The network that we are trying to create should look something like the diagram below:
In this picture the red network is the real world network to which the host machine is connected. The green network is a virtual network that has been created by the virtualization software to connect the virtual machines.
I believe that this type of approach could also be used to test such things as web protege/protege 3 server/protege 4 server and firewalls with configurations such as port forwarding.
Setting up the network
To set up this virtual network, you will need to set up two virtual machines that will be networked together. The first machine that needs to be set up is the machine on which you are going to test the behavior of Protege. Once you start playing with Protege and virtual machines, such machines might be useful to collect so that you can easily answer questions about Windows 8, Ubuntu and such. I won't describe how this machine is set up too much here but it is pretty simple. Essentially you configure the virtual hardware of the virtual machine, find some installation media and install the operating system to the virtual machine. You can use any virtualization software that you like but I am using VirtualBox and the virtual machine that I provide for the firewall is a VirtualBox virtual device.
Next you need to setup a virtual firewall device. In this example I am working with the endian firewall. If you are working with VirtualBox, then you can take a shortcut and retrieve a working version of such a virtual firewall from here. It is also not too difficult to put such a firewall together from scratch (if for example you are working with other virtualization software such as vmware}. There is an excellent and fun online course that describes how to setup such a network either using VirtualBox or VMware.
If you create a virtual network in this way, the virtual firewall machine will have two virtual network interfaces, the external network interface (the red one) which points to the network of the host machine, and another network interface (the green one) which can be shared by other virtual machines. The virtual machine for testing Protege should be configured to point to the green network of the endian firewall. The endian firewall can be configured by accessing the web page https://192.168.0.15:10443 on the green network.
Configuring the firewall
Now, for this particular test we want to configure the firewall to deny outgoing web requests but to provide a proxy for those web requests. We can configure the firewall by using a very nice web interface to the firewall from any virtual machine on the green network. When the endian firewall starts up, it displays a nice message telling us what web address to use to manage the firewall: Management URL: https://192.168.0.15:10443 and this is the url that we use to connect to the firewall. If you use my preconfigured virtual endian firewall then the username is admin and the password is vmproxynet. Otherwise the user name and password are as you configured them when you set up the firewall. I made the following changes:
- I went to the firewall tab and then clicked "Outgoing traffic". From there I disabled the two firewall rules that allowed outgoing http and https traffic. As a result of this, machines on the green network are no longer able to access web pages and Protege will not be able to access many ontologies on the web including the proverbial pizza ontology.
- I went to the Proxy tab and enabled a non-transparent http proxy on port 8080.
At this point it should be possible to test the configuration with a web browser on the green network. By default, the web browser should not be able to access web sites such as google.com because web access is being blocked by the browser. However, if the browser is configured to use the proxy at 192.168.0.15:8080 then web access should resume working because the http proxy on the firewall is providing access to external web pages.
Testing Protege
In this configuration, an unmodified copy of Protege on a virtual machine on the green network will not be able to connect to ontologies on the web and it will not be able to get updates from the network. But if you change the protege configuration as described in Working with firewalls and proxies, Protege will again be able to both access ontologies on the web as well as get updates.