Protege4ClientServerAdvancedInstallation
Hopefully at the point of the release we will have automated the installation process and these pages will be for advanced users.
The purpose of these pages is to allow people to know what is installed by the server installation and what options the user can change. The installation setup is slightly different depending on whether the operating system in question is Linux, OS X or Windows. The Protege Server should run on other platforms as well though we don't yet support its installation. The key things that need to be figured out for an installation to some other platform is obtaining a version of Java that is at least Java 1.6 and determining how to make the Protege 4 Server start at boot time.
Contents
The protege user account
Depending on a Protege server administrators security requirements, the administrator may want to run the Protege server from a unprivileged system account. The Protege server does not require very many privileges; it requires a port that it can listen on and read-write access to a portion of a file-system. For this reason, in accordance with the principle of least privilege, it makes sense that the Protege server should run under a user account that is distinct from any user account (so that it does not necessarily have the potential to access any user files) and distinct from any account with special privileges such as the root account.
We are attempting to support this mode of operation in the scripts that allow Protege to run as a daemon on the linux, os x and windows platforms. The current status is that
- on linux we have worked out all the details and have the Protege server running on a couple of machines in this mode. The command to create a system user on a linux system is as follows:
adduser --system --home /usr/local/protege protege
- on os x we have the ability to specify the user account which will run the Protege server but we have not yet determined how to make the account be a system user account rather than a regular user account. There is a discussion on the web describing how use directory services to make this work and I seem to remember this from the days when I was an OS X user.
- we don't yet have the daemon mode working at all on windows.
Linux
On a linux system the following files and directories are created:
- /usr/local/protege which contains the core server installation in the subdirectory server, the users data files in the subdirectory data and some command line utilities in the bin subdirectory.
- /etc/init.d/protege which is a script that ensures that the Protege server is started at boot time.
- /etc/default/protege which is a properties file that configures the init.d script above. The user will have to modify this file before the server will run correctly.
- /etc/rc#.d/K20protege which are a symbolic links to /etc/init.d/protege for '#=0,1,6'. These scripts ensure that the Protege Server is correctly shutdown when the computer stopped. In particular, if the sever has unsaved files (a temporary condition in any case) this script give Protege some time to save the files before the system exits. The best way to configure these files is through the update-rc.d script as explained below.
- /etc/rc#.d/S20protege which are symbolic links to /etc/init.d/protege for '#=2,3,4,5'. These scripts ensure that the Protege Server is running at system startup. The best way to configure these files is through the update-rc.d script as explained below.
When the protege server runs, it will write some system logs to the /var/log/protege directory.
An example/etc/default/protege file looks like this:
# # This file goes into /etc/default/protege and holds the default # settings for the Protege Server. # HOSTNAME=`hostname` PROTEGE_SERVER_PREFIX=/usr/local/protege PROTEGE_SANDBOX_USER=tredmond JAVA_CMD=/usr/local/java/jdk1.7.0_06/bin/java PID=/var/log/protege/PID
The HOSTNAME property tells the Protege 4 server how to advertise itself to the world. On a well-configured desktop or server machine that is not hidden by NAT the given setting will probably usually work. If not an IP address works fine. The sandbox user parameter is important and must be changed. This is a user account on the system that is set aside to run the server. Ideally it would be a user account that has minimal access to the system as a whole excepting write access to the /usr/local/protege/data directory. <p/> To configure the /etc/rc#.d scripts first install the protege script into the /etc/init.d directory. Then run the sudo update-rc.d protege defaults command and the results should look something like this:
Neptune:init.d% sudo update-rc.d protege defaults Adding system startup for /etc/init.d/protege ... /etc/rc0.d/K20protege -> ../init.d/protege /etc/rc1.d/K20protege -> ../init.d/protege /etc/rc6.d/K20protege -> ../init.d/protege /etc/rc2.d/S20protege -> ../init.d/protege /etc/rc3.d/S20protege -> ../init.d/protege /etc/rc4.d/S20protege -> ../init.d/protege /etc/rc5.d/S20protege -> ../init.d/protege Neptune:init.d%
The Server can be stopped with the command
sudo /etc/init.d/protege stop
The Server can be started with the command
sudo /etc/init.d/protege start
The Server can be restarted with the command
sudo /etc/init.d/protege restart
The following command will make a first cut estimation of the status of the server:
sudo /etc/init.d/protege status
OS X
On an OS X system the following files and directories are created:
- /usr/local/protege which contains the core server installation in the subdirectory server, the users data files in the subdirectory data and some command line utilities in the bin subdirectory.
- /Library/LaunchDaemons/org.protege.owl.server.plist which is a launchctl file to ensure that the Protege Server starts at boot time. This file must be editted in order for the Protege Server to be automatically started.
When the protege server runs, it will write some system logs to the /var/log/protege directory.
<p/>
The launchctl file is as follows
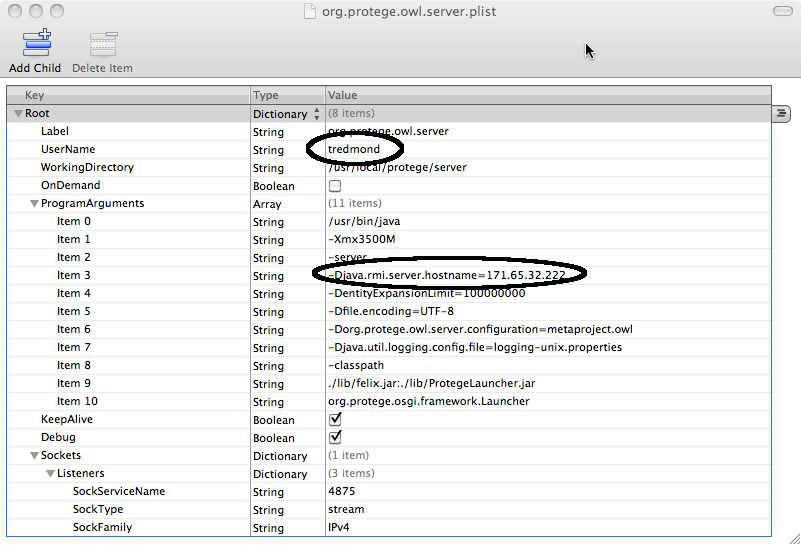
The two options that must be changed are circled in the above diagram. As in the Linux case, the username is the user under which the Protege server runs. Ideally this user has minimal access to the system as a whole except for write access to the /usr/local/protege/data and /var/log/protege directories.
The server can be restarted with the command
sudo launchctl stop org.protege.owl.server
It will restart immediately after stopping.
Windows
To be determined.